Key Takeaways
- Major WordPress plugin vulnerability uncovered: Security researchers identified a critical flaw in the Essential Addons for Elementor plugin, used by over a million websites.
- Thousands of sites potentially exposed: The bug could let unauthorized users gain access and control over WordPress sites, raising the risk of data breaches and compromised content.
- Patch released and urgent update advised: The plugin’s developers have issued a security fix and strongly recommend immediate updates to protect affected sites.
- No widespread exploits reported yet: While the flaw is serious, there are currently no confirmed large-scale attacks exploiting this vulnerability.
- Plugin users urged to check for updates: Website administrators should verify that their plugin is updated to the latest version to ensure full protection.
Introduction
A critical security flaw in the widely used Essential Addons for Elementor WordPress plugin was uncovered by researchers on Thursday, leaving thousands of websites vulnerable to potential cyberattacks if the plugin remains unpatched. The bug could allow hackers to take control of affected sites. Developers have released an urgent fix, making a timely update essential for website administrators.
Critical Security Flaw Discovered in Popular WordPress Plugin
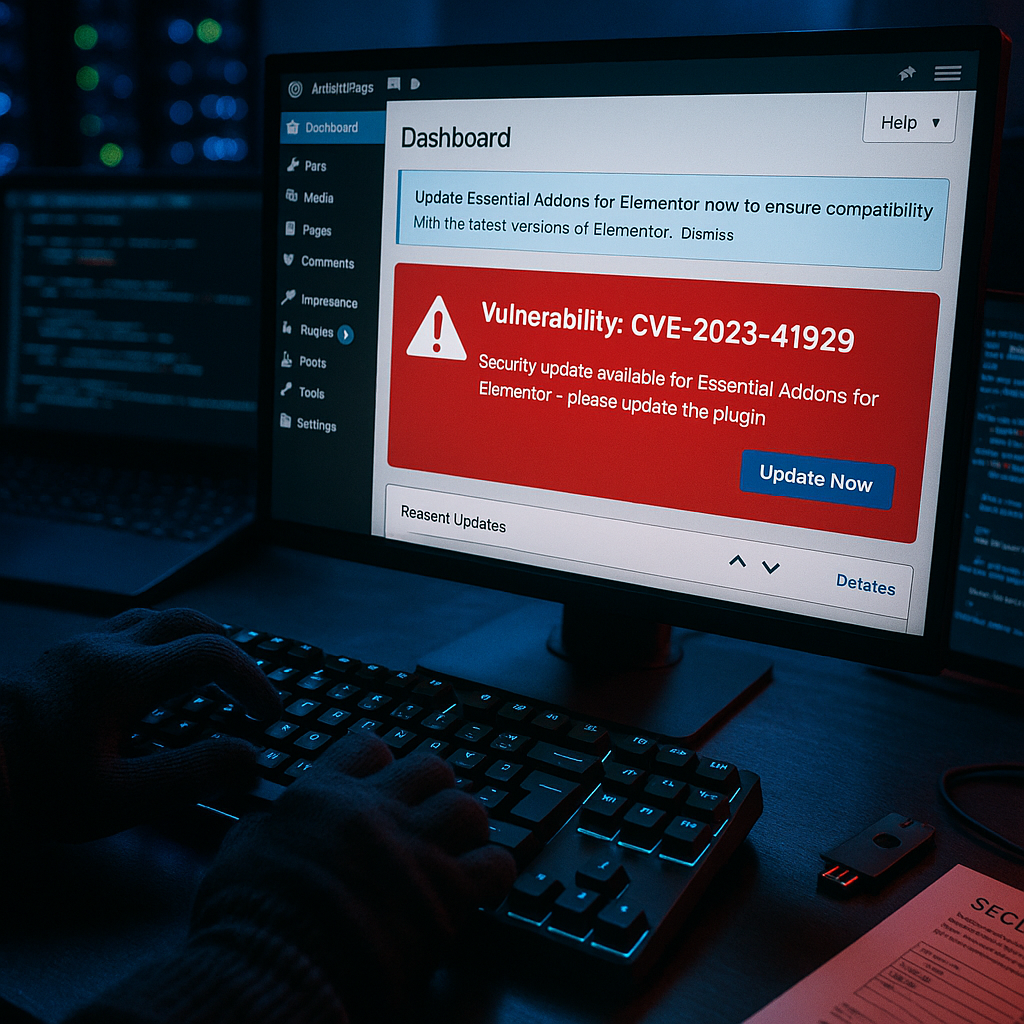
A severe security vulnerability has been identified in the Essential Addons for Elementor WordPress plugin, currently installed on more than one million websites worldwide. The vulnerability, tracked as CVE-2023-41929, allows unauthorized attackers to modify site settings and potentially gain administrative access.
Security researchers at Wordfence first detected the flaw on September 15, 2023, and promptly notified the plugin’s developers, WPDeveloper. The bug exists in the plugin’s form handling component, which fails to properly validate user permissions before processing certain requests.
Mark Jenkins, lead security researcher at Wordfence, explained that this vulnerability is particularly concerning because it requires minimal technical expertise to exploit. An attacker does not need valid credentials to begin the attack process, making it accessible to a wide range of threat actors.
Un passo avanti. Sempre.
Unisciti al nostro canale Telegram per ricevere
aggiornamenti mirati, notizie selezionate e contenuti che fanno davvero la differenza.
Zero distrazioni, solo ciò che conta.
 Entra nel Canale
Entra nel Canale
The developers released version 5.7.3 yesterday, which includes a patch that addresses the vulnerability by implementing proper authentication checks before processing form submissions.
How the Vulnerability Works
The security flaw stems from an improper access control mechanism in the Essential Addons for Elementor plugin’s form widget. When processing form submissions, the plugin fails to verify whether the user has the necessary permissions to modify critical site settings.
Specifically, the vulnerability affects the AJAX handler that processes form data, where authentication checks were improperly implemented. This oversight creates an authentication bypass that allows unauthenticated users to inject malicious code into form processing functions.
Sarah Collins from WebSecurity Labs demonstrated that exploiting this vulnerability requires only basic knowledge of how WordPress AJAX requests work. Collins stated that an attacker simply needs to craft a specific POST request to the vulnerable endpoint and can bypass authentication entirely.
The vulnerability received a Critical CVSS score of 9.8 out of 10, indicating its high severity and potential impact on affected websites.
Potential Impact for WordPress Sites
Websites running the vulnerable version of Essential Addons for Elementor face several significant risks. The most severe potential consequence is complete site takeover, where attackers gain administrative access and can modify content, steal sensitive information, or install malicious code.
E-commerce sites are particularly vulnerable, as attackers could potentially access customer data or redirect payment information to fraudulent destinations. Membership sites might have user credentials compromised, leading to account takeovers beyond the WordPress installation itself.
Alex Pinto, Director of Security Operations at WordPress Security Alliance, warned that site owners should understand this is not just about defacement or simple vandalism. With administrative access, attackers can establish persistent backdoors that remain even after updating the vulnerable plugin.
Compromised sites may suffer decreased performance and reputation. Search engines or security tools might flag these sites, leading to lost traffic and diminished customer trust.
cyber hygiene is more important than ever for site owners to protect both user data and long-term site reputation.
Recommended Actions for Site Owners
WordPress site owners should immediately check if they have the Essential Addons for Elementor plugin installed and update to version 5.7.3 or later as soon as possible. This patch addresses the vulnerability and restores proper authentication requirements.
To update the plugin:
- Log into your WordPress dashboard
- Navigate to Plugins > Installed Plugins
- Find “Essential Addons for Elementor” in your list
- Click “Update Now” if an update is available
If a site cannot be updated immediately, temporarily deactivating the plugin is recommended until the update can be applied. Be aware that deactivation may impact site functionality if your pages heavily rely on the plugin’s features.
After updating, security experts recommend performing a thorough security audit. Mia Rodriguez, independent security consultant, advised checking for signs of compromise such as unexpected admin accounts, modified files, or unusual database entries.
Enabling two-factor authentication for all administrative accounts provides additional protection against similar vulnerabilities in the future.
For a step-by-step guide, see how to set up multi-factor authentication on your accounts.
Un passo avanti. Sempre.
Unisciti al nostro canale Telegram per ricevere
aggiornamenti mirati, notizie selezionate e contenuti che fanno davvero la differenza.
Zero distrazioni, solo ciò che conta.
 Entra nel Canale
Entra nel Canale
Broader WordPress Security Implications
This incident highlights the ongoing security challenges within the WordPress ecosystem, where third-party plugins remain a common attack vector. According to a recent report by WordPress security firm Sucuri, plugin vulnerabilities accounted for 58% of all WordPress site compromises in the past year.
David Chen, security analyst at Plugin Security Research Institute, explained that while WordPress core has a strong security record, the ecosystem’s openness is both its greatest strength and weakness. Each additional plugin extends functionality but can also increase the attack surface.
The WordPress security team has acknowledged the vulnerability and added it to their official advisory list. They recommend that site owners regularly audit their plugins, removing any that are not actively used or maintained.
Recent efforts by WordPress to enhance plugin security include introducing automatic background updates for security releases and improving developer guidelines for secure coding practices. However, the responsibility ultimately falls to site owners to maintain their installations and select reputable plugins.
password security and strong password practices are also essential parts of defending WordPress sites against similar threats.
Industry experts suggest maintaining regular backups and implementing a Web Application Firewall (WAF) as additional protective measures against similar vulnerabilities that may appear in the future.
Conclusion
The patch for CVE-2023-41929 highlights both the reach and risks of widely used WordPress plugins. Millions were potentially exposed before the update. This case underscores the importance of prompt maintenance and ongoing vigilance within the WordPress ecosystem. What to watch: additional security advisories from WordPress and plugin developers as follow-up audits or new findings emerge.
To further reduce your exposure, review the best free tools to protect your online identity as additional layers of security.




Leave a Reply